In a continuation of my previous adventures with removing Bitcoin malware described here, I ran into a vastly superior method of hijacking your CPU power to mine cryptocurrency. In the past, we’ve seen a ton of typical malware running EXE files in plain sight with very easy removal steps and no sophistication whatsoever. This is very different.
Couple of disclosures first:
- This is original research. There are many reports of these infections, and AV companies like ESET, Webroot, and Symantac do have solutions to these problems. Some of them actually work, too! What I have not been able to find on the net is the actual source code to the miner. Read on.
- We have the source code. I am posting this at the bottom of this article in an altered form that cannot be re-used for malicious purposes. The code is very readable and sheds a lot of light on how sophisticated these attacks have become.
- After extracting the source code, I did lots of online searches and found an excellent whitepaper written about this specific malware. It’s written in Turkish. I can’t read Turkish but I can paste text into Google Translate very well.
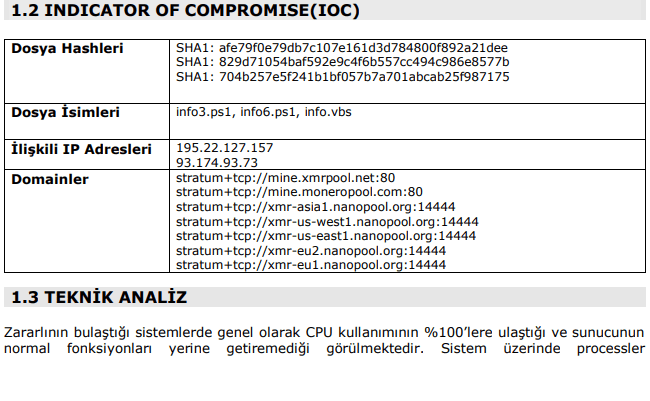
Turkish 101 optional. It’s pretty clear to see what the researcher was trying to communicate here. IP addresses, port numbers and DNS names listed in a nice, coherent table.
- The IP addresses disclosed are real and wildly reported as malicious. Locating these addresses is key in regaining control over the infected machine. These might be different for your specific infection.
- This isn’t really a Bitcoin miner as CPU mining of Bitcoin is no longer feasible. ‘Monero’ is being used here but in reality this is of no importance as command and control center is capable of sending instructions to switch to whichever crypto they want.
Finding the Problem
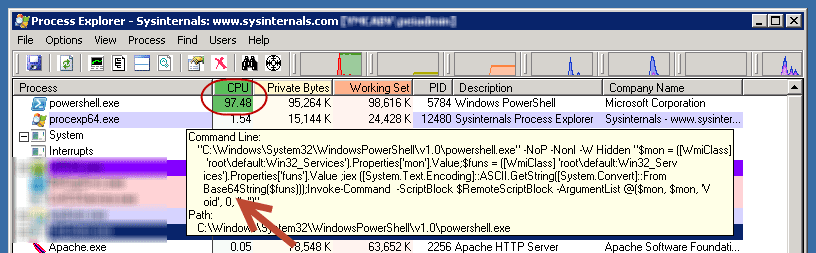
Normally you’d look for an EXE file that is causing excessive resource consumption and attack it from there. Good luck doing that when the file is powershell.exe.
You could just disable PowerShell altogether. This may be an OK workaround on a workstation, but If you’re on an Exchange server or a DC this will literally break everything under the sun. And in case you’re wondering, changing PS Execution Policy AFTER you’ve been infected does nothing.
As usual “procexp64” from Sysinternals is your first weapon of choice. We’re going to do 2 things with it:
- Identify what code is actually running (since there is no EXE, how can you tell?)
- Enumerate the TCP connections and block them later on. This is annoyingly time consuming but it works.
The first picture above prints out the commands being used to mine; the output is very sparse though, and you can tell right away variables are being chained and obfuscated using text encoding. Take a look at that big red arrow in the screenshot, looks familiar? Long story short Powershell has the ability to parse Base64 encoding and a few clicks later we have insight into everything the software is up to.
Source Code Link
Powershell Malware Sanitized Text File
Source Code posted here is provided for reference. It has been modified and key parts removed to prevent this malware from being re-used.
Parsing the Source Code
Number 1 priority is to cut off network access to the command&control system. This is important because the command and control can issue any instructions to your server. If the attacker gets tired of mining crypto currency with your servers, they could very easily set off a ransomware infection. Or just delete all your files.
Number 2 priority is to cut off network access to the ‘mining pool’. Mining in itself isn’t harmful to your systems in any way, it merely consumes LOTS of resources which in turn is crowding out legitimate windows processes and causing them to crash.
Number 3 priority is actually removing the infection. This will have to be a future blog post as it is an adventure in itself.
JacobR, PEI




