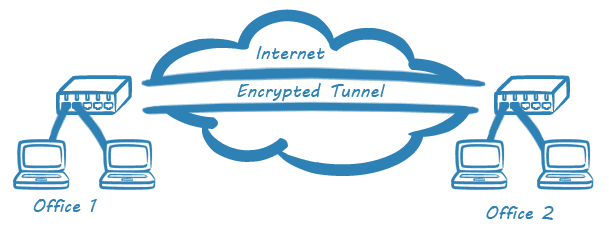
We had an issue where we could not poll a Cisco ASA with SNMP from through the VPN tunnel. When we looked at the tunnel stats via “show crypto ipsec sa peer <peer-ip-address>” we could see traffic was being decrypted from the polling station and getting to the ASA firewall, but would not be encrypted from the ASA back to the polling station. What we found was that the firewall was setup with a route pointing for the remote polling network (10.55.0.0/16) that was pointing out the outside interface
route outside 10.55.0.0 255.255.0.0 50.235.209.137
This was causing the SNMP responses from firewall to go straight out to the internet ISP. When we removed this route, the return traffic would get encrypted and sent across the VPN to the polling station as desired. It should be noted that non ASA bound traffic would go across the VPN in either case, but only return traffic from the ASA would get miss routed based upon the specific outside route statement.
Jason Howe, PEI




