
Cisco announced on July 10th, 2019 that there is a vulnerability in the cryptographic driver for Cisco ASA software and FTD software that could allow an unauthenticated, remote attacker to cause the device to reboot unexpectedly. Most of the information below comes from the Cisco official advisory.
CSCvp36425:
The vulnerability is due to incomplete input validation of a Secure Sockets Layer (SSL) or Transport Layer Security (TLS) ingress packet header. Only traffic directed to the affected system can be used to exploit this vulnerability. This vulnerability affects systems configured in routed and transparent firewall mode and in single or multiple context mode. It can be triggered by IPv4 and IPv6 traffic. A valid SSL or TLS session is required to exploit this vulnerability. Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
Affected Products:
This vulnerability affects the following Cisco products if they are running a vulnerable release of Cisco ASA Software or FTD Software:
- ASA 5506-X
- ASA 5506-X with FirePOWER Services
- ASA 5506H-X
- ASA 5506H-X with FirePOWER Services
- ASA 5506W-X
- ASA 5506W-X with FirePOWER Services
- ASA 5508-X
- ASA 5508-X with FirePOWER Services
- ASA 5516-X
- ASA 5516-X with FirePOWER Services
There are multiple features that, when enabled, cause Cisco ASA Software or FTD Software to process SSL/TLS packets. These features include, but are not limited to
- AnyConnect and Clientless SSL VPN
- HTTP server used for the management interface
Verification of Vulnerability
Use the show asp table socket | include SSL|DTLS command. If any output is provided, the device is vulnerable. Example of vulnerable device below:
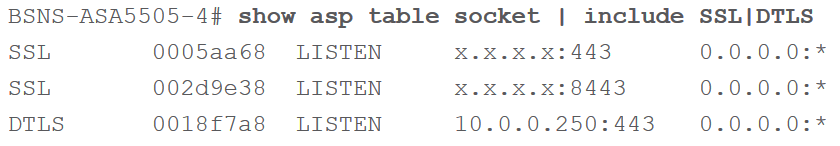
Products Confirmed Not Vulnerable
Cisco has confirmed that this vulnerability does not affect the following Cisco products:
- 3000 Series Industrial Security Appliances (ISAs)
- 7600 Series ASA Services Module
- Adaptive Security Virtual Appliance (ASAv)
- ASA 1000V Cloud Firewall
- ASA 5505
- ASA 5510
- ASA 5512-X
- ASA 5515-X
- ASA 5520
- ASA 5525-X
- ASA 5540
- ASA 5545-X
- ASA 5550
- ASA 5555-X
- ASA 5580
- ASA 5585-X
- ASA 5512-X with FirePOWER Services
- ASA 5515-X with FirePOWER Services
- ASA 5525-X with FirePOWER Services
- ASA 5545-X with FirePOWER Services
- ASA 5555-X with FirePOWER Services
- ASA 5585-X with FirePOWER SSP-10, SSP-20, SSP-40, or SSP-60
- Catalyst 6500 Series ASA Services Module
- Firepower 2100 Series
- Firepower 4100 Series
- FirePOWER 7000 Series Appliances
- FirePOWER 8000 Series Appliances
- Firepower 9300 Security Appliances
- Firepower Threat Defense Virtual (FTDv)
- Industrial Security Appliance 3000
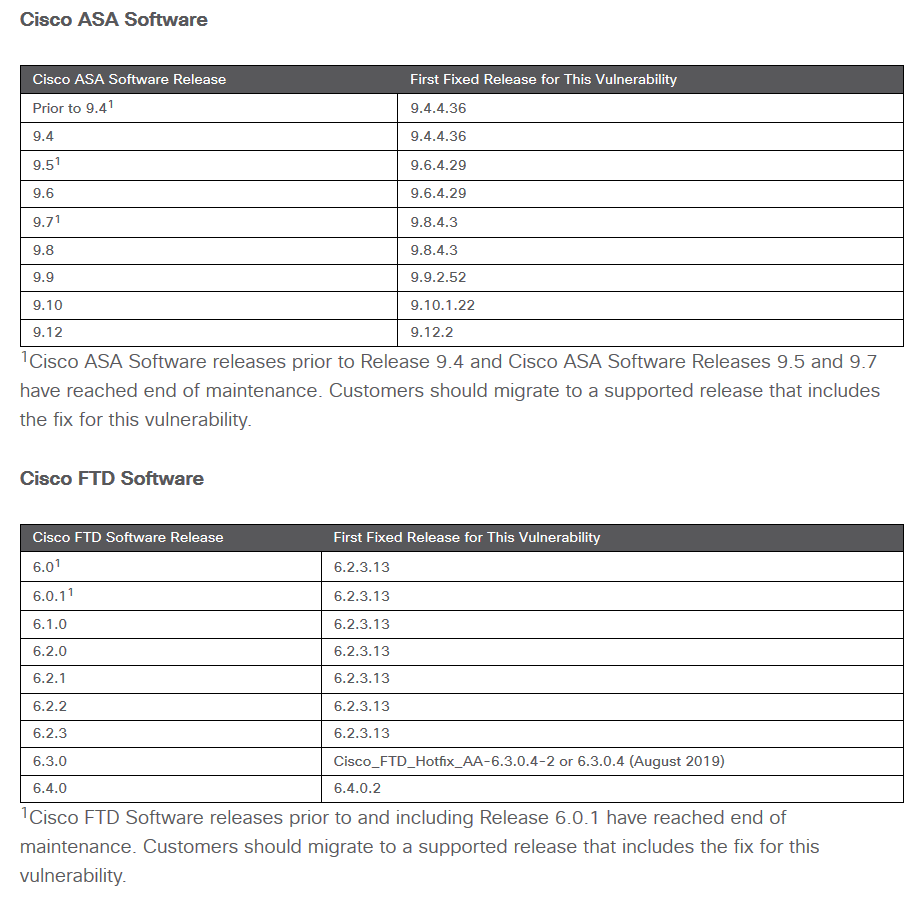
Fixed Software
Alison Wallick, PEI




