You’re probably tired of hearing how cybersecurity attacks are becoming more advanced, and you need to adapt. But the fact of the matter is that it’s true and you do.
In the changing cybersecurity landscape, SIEM and SOC solutions play a crucial role in staying ahead of the latest threats and attacks. Every business can benefit from a SIEM and SOC integration, but it’s essential for those dealing with sensitive data or facing regulatory requirements. When used together, SIEM and SOC act as an effective toolset against malicious activity, providing your business with continuous monitoring, data collection, and quick detection of suspicious activity.
So, what really are SIEM and SOC solutions, and why are they so important?
What is a SIEM?
A SIEM is a Security Information and Event Management solution, and it serves as a centralized log management system that stores data collected from across your IT environment. The collected data includes information such as network devices and traffic, user activity, endpoint data, applications such as email, and more.
SIEM solutions analyze the thousands of collected data points to monitor for signs of suspicious behavior. When the SIEM detects suspicious activity, it triggers alerts based on unique rules the company creates. A SIEM can also generate audit reports to demonstrate compliance, and in the case of an event, SIEM logs aid in recovery efforts.
What is a SOC?
A SOC, or Security Operations Center, receives data and alerts from your SIEM—or another threat detection system—to monitor and respond to detected threats. The SOC response services use automation, but they still require a human element to ensure accurate readings of alerts and to effectively address particularly dangerous threats.
The SOC element of threat detection and response adds to a comprehensive security approach that is necessary in the new cybersecurity landscape. A SOC can also be paired with Managed Detection and Response (MDR) services to deliver 24/7 attack prevention, detection, and remediation. This approach enables targeted and risk-based threat hunting which reduces the risk of downtime and the remediation costs associated with incidents.
What is MDR?
Managed Detection and Response (MDR) is a solution that allows businesses to outsource some of their security operations to a third party, specifically monitoring and alerting tasks. MDR allows for advanced threat detection and proactive threat hunting to ensure a company is equipped with a proactive security strategy, but also able to react quickly and effectively. When paired with a SOC, MDR can elevate a business’s security strategy.
The frequency of cyber-attacks has been increasing, with the global average cost of a data breach in 2023 reaching $4.45 million, a 15% increase over three years according to IBM’s 2023 Cost of a Data Breach Report. Therefore, early threat detection is crucial, and MDR and SOC services are two of the most effective ways of catching threats in their initial stages.
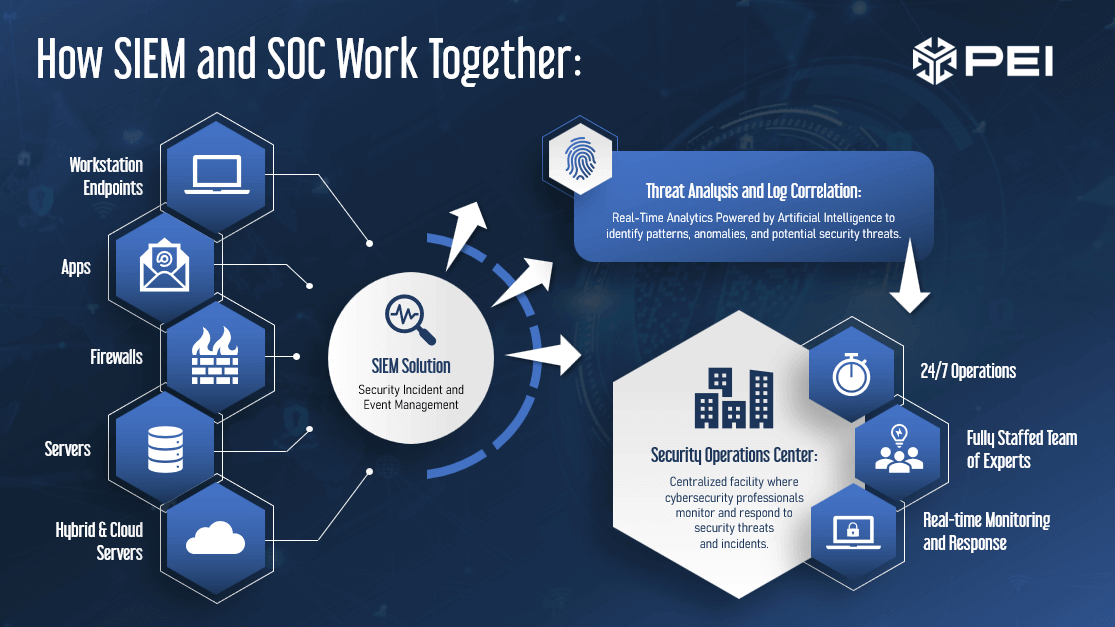
How do SIEM and SOC Work Together?
SIEM and SOC solutions work together to create a security strategy focused on alerting and reaction, rather than just prevention. Given today’s advanced attacks, it’s increasingly likely that a hacker is going to make their way into your environment at some point. You need to be prepared when this happens.
The SIEM is responsible for monitoring behavior, analyzing security data across an environment, and generating alerts for potential threats. As the SIEM identifies potential threats, it sends alerts to the SOC for investigation and response. If the SIEM detects a potential threat, it isolates the incident to prevent damage to systems. The threat can then be evaluated to determine if it’s a serious concern or false positive. The security specialists at the SOC will be notified of the potential threat and investigate the origin of the attack, perform additional analysis, and determine the severity of the potential threat before taking further action. The collaboration between SIEM, SOC, and MDR solutions streamlines operations, improves incident response, and strengthens an organization’s security posture.
What are the Benefits of SIEM and SOC?
If I haven’t already convinced you that SIEM and SOC are necessary additions to your security strategy, these 6 key benefits just might.
Centralized Security Alert System
SIEM and SOC offer a centralized system for threat detection, alerting, and remediation, so you don’t have to jump from system to system in order to analyze and possibly respond to potential threats. With all your alerting hosted in one place, it’s easy for you to create custom security rules, and then monitor and enforce them all within one system.
Around the Clock Monitoring
Using SIEM and SOC solutions provides your business with 24/7/365 monitoring and alerting. SIEM will constantly have eyes on your environment scanning for suspicious behavior and a SOC is available to evaluate alerts and take next steps. You can rest easy knowing your environment is secure even when you’re not there to watch it.
Isolate Attacks
In the event of a breach, the SOC can isolate the attack without shutting down all operations. Once alerted, the SIEM can cut off the breached endpoint from the remainder of the environment to prevent a hacker from elevating any access permissions or obtaining your data. Meanwhile, the SOC has time to analyze the alerts and determine if the threat is legitimate and what action to take. This means your systems can remain operational and secure in the event of a breach that is detected early.
Increased Awareness of the Environment
SIEM solutions collect data from across your entire IT environment, and therefore have improved context of the regularly occurring activity in your environment. Because the system has a more nuanced understanding of the way your environment runs, it is better able to detect more sophisticated attacks that might otherwise fly under your radar.
Reduce Alert Fatigue
When your IT team is constantly bogged down with security alerts, it can lead to alert fatigue. Especially when your team has other tasks they need to focus on simultaneously. It can be difficult to identify what are actual threats versus false positives. With custom rules in place, your SIEM solution can take on some of this analysis for you. Then, with a SOC in place, your team can take the evaluation and remediation tasks off their plate so they can focus on other work at hand.
Regulatory Compliance
Many industries have regulations—such as HIPAA—in place that require businesses to keep data logs for certain spans of time and even provide security reports. A SIEM solution can provide you with real-time logs and reporting features to ensure that your log monitoring and threat detection is up to industry standards. If you aren’t in an industry that has data compliance regulations, you might want cybersecurity insurance for your business. Many cybersecurity insurance companies are now requiring this type of advanced threat detection and response, and if you are out of compliance, you will find that you aren’t covered in the event of a breach.
Start Building Your Comprehensive Security Strategy
SIEM and SOC can be confusing, but they are instrumental tools in any security strategy. If you are looking to get started with these security solutions, PEI can offer a closer look at the tools and talk you through how they can work for your business.
You deserve to rest easy knowing your business is secure when you’re not there (and even when you are). Contact PEI today and integrate SIEM and SOC into your comprehensive security strategy!
Matt Dixon, PEI




