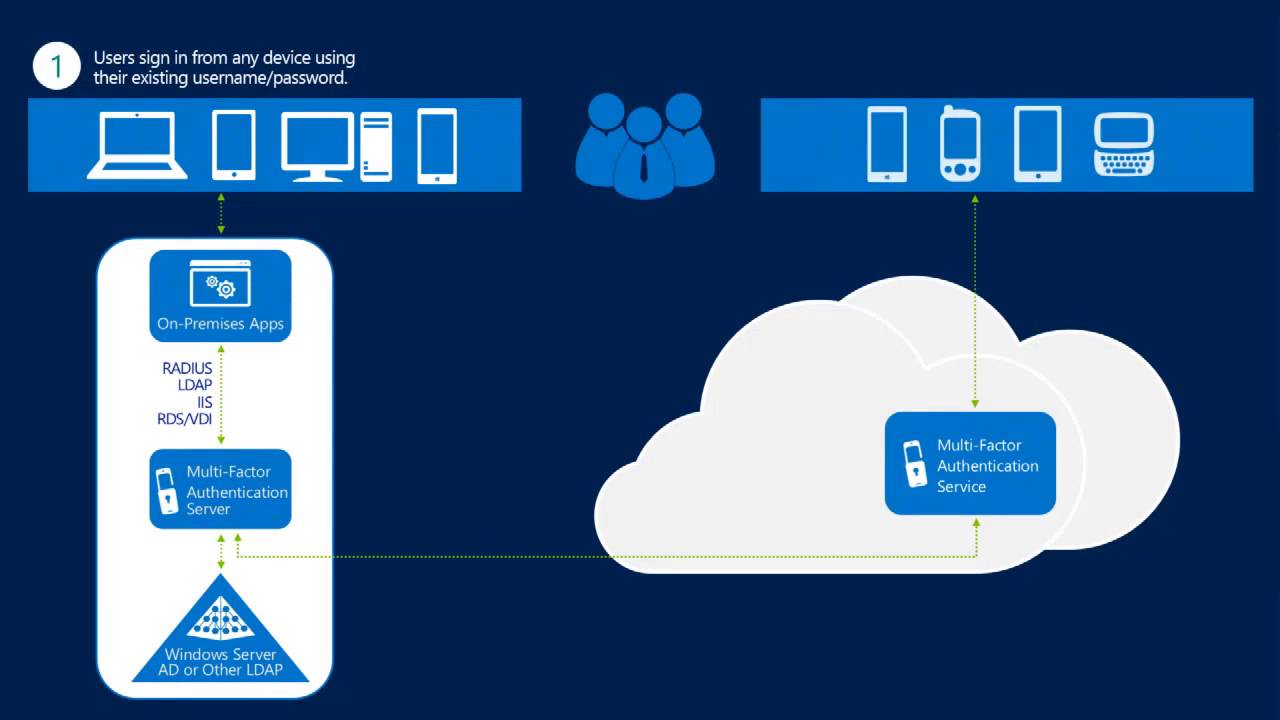
Here is some basic knowledge on Multi-Factor Authentication (MFA) for Office 365 and Azure. What is cool about this is you can now use it to customize caller ID and flag fraud alerts, among other things.
Multi-Factor Authentication Fraud Alert
This is a great security feature! If your users receive a multi-factor authentication request when they aren’t expecting it (maybe they are golfing, shopping, having their nails done, attending night classes, or watching the Seattle Seahawks win the Super Bowl!), they can ignore the call or answer and hang up without pressing # to deny access to the person attempting to use their credentials.
The fraud alert feature also takes it a step further and allows your user to be more proactive about attempted attacks. They can answer the phone and enter their configured fraud alert code (0# by default, but customizable) to report the attempted access. Not only will it deny the authentication taking place, but will put a block on that user’s account so that additional authentication attempts are automatically denied without continuing to bother the user. It can also send an email notification to any configured email addresses such as the security team and IT admins so that they can take action, investigate, and change the user’s password. Once they have taken appropriate action, they can unblock the user’s account in the MFA Management Portal.
Multi-Factor Authentication with Office 365 & Azure

Now that multi-factor authentication is included with Office 365 user licenses as well as administrator access to Azure, there might be some questions about the additional features you can get with Microsoft Azure Multi-Factor Authentication. The chart below shows the feature comparison.

The Multi-Factor Authentication Management Portal
The primary features that Microsoft Azure Multi-Factor Authentication unlocks are those found within the Multi-Factor Authentication Management Portal, which can only be accessed after creating a Multi-Factor Auth Provider in the Azure Management Portal. Creating that provider and linking it to an Office 365 directory are what upgrade an Office 365 tenant from having Multi-Factor Authentication for Office 365–with a subset of features–to having Microsoft Azure Multi-Factor Authentication, which contains all of the available features. View this post from Microsoft to learn how to get started.

To create a Multi-Factor Auth Provider sign into the Azure Management Portal and go to Active Directory, then Multi-Factor Auth Providers. Create a new provider by providing a name, usage model for billing and link it to your directory unless being used for on-premises applications only.
Let’s go over some of the things you can do in the MFA Management Portal to take advantage of these additional features. The features are accessed by managing your Multi-Factor Auth Provider.

To access the MFA Management Portal, select a Multi-Factor Auth Provider and click Manage.

Here, we can see the advanced features accessed through the Multi-Factor Authentication Management Portal.
Beth Zange-Sellers, PEI




