Azure Advanced Threat Protection is a cloud-based tool (E5 Needed) designed to help detect breaches of your physical, virtual, or Azure-hosted Domain Controllers. This tool is especially useful if you find yourself running a Hybrid AD where AD servers on premises are essentially processing logins from (hopefully) your uses over the internet. In a disaster scenario, where account credentials are compromised (or accounts are locked out) with an O365 tenant, Microsoft support might assist you in blocking false logon requests to your tenant. But, when your Identity source is on premises, what can you do?
Azure ATP – Functionality
The number 1 thing you can do is monitor logon attempts and generate old school email alerts that let you know when your infrastructure is in trouble. With Azure Advanced Threat Protection, the alert data is generated on your DCs and transferred over to M365, which will itself send an email notification, thus removing reliance on your Exchange server to deliver notifications.
Additional functionality of Azure ATP is monitoring for Zone Transfers in your DNS. Once an attacker gains foothold in your network, redirecting DNS is a popular way of stealing additional credentials or pointing your users to malicious websites littered with Malware in order to strengthen the attacker’s foothold in your environment or simply cryptolocker all your data.
Azure ATP can also detect and alert on other suspicious activity, like attempts at crawling your AD forest for the purpose of enumerating security groups and OUs (think searching for Domain Admins).
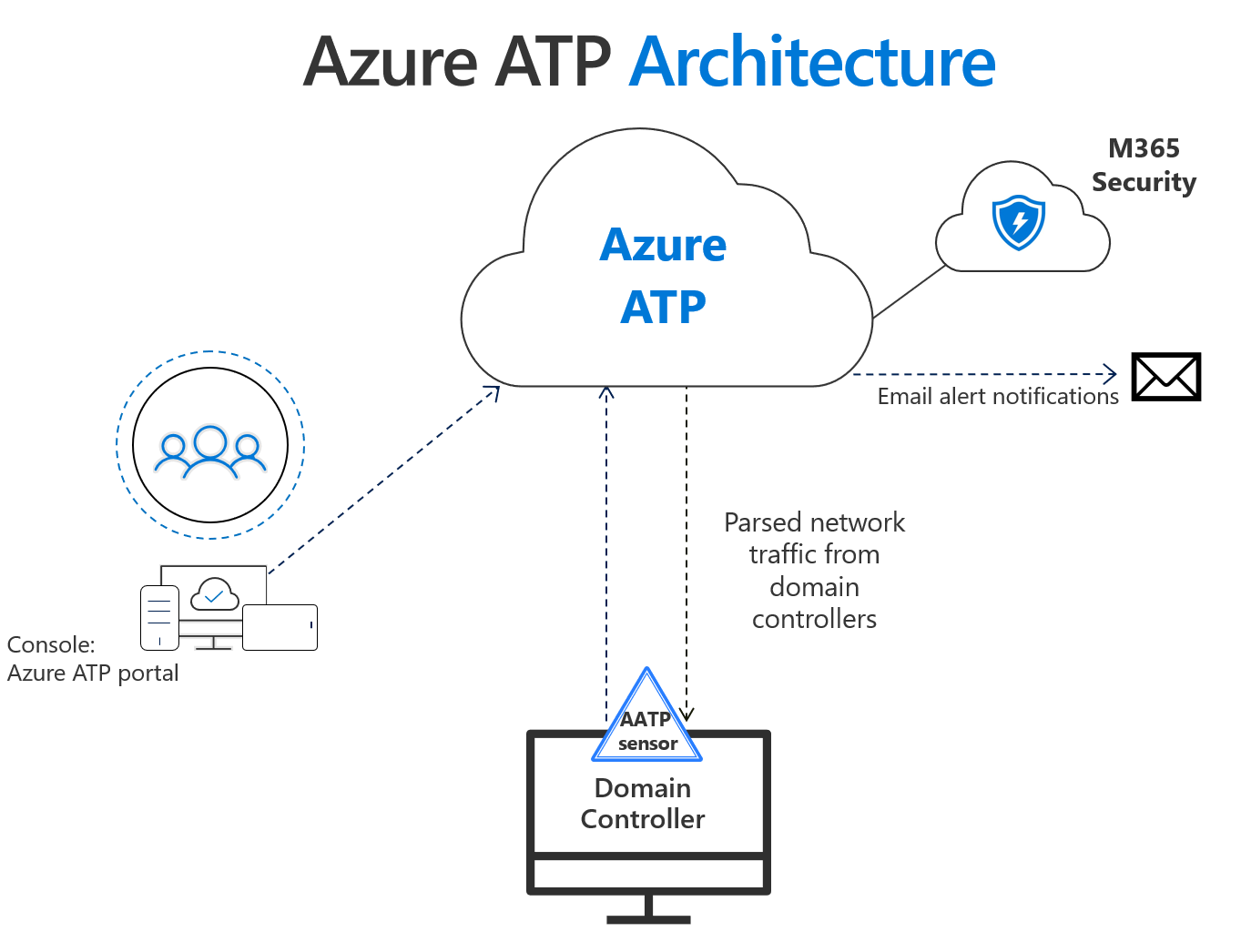
Azure ATP – Components
Azure Advanced Threat Protection is a small, resource-constrained, installable component to be put on your Domain Controllers. The component communicates with M365 and sends you alerts. Simple. But what if you’re unable (think server core) or unallowed to install anything on your DCs?
This is where a ‘standalone Azure ATP sensor’ comes into play. It’s a ‘fatter’ version of the Azure ATP installable–think of it as a log collector. The standalone sensor can collect and aggregate data from multiple Domain Controllers, physical and virtual. The only extra piece you need for standalone sensor to work is port mirroring. Since Azure ATP relies on Deep Packet Inspection, port mirroring (or direct installation on DC) is required. For HyperV or ESXi, port mirroring can easily be handled with a few virtual network configurations (must account for VMware HA or HyperV failover cluster) whereas monitoring a physical DC requires port mirroring on physical switches and additional configuration on the Standalone ‘collector’ to see the data being shipped over from the DC.
Azure ATP – Limitations
Keep in mind Microsoft does not claim Azure ATP to be an IPS and only advertises this solution as a part of your IDS strategy, specifically outlining there is no ‘action’ being taken when an alert is generated. Meaning, while you will be alerted of suspicious activity, there is no automatic remediation component at this point (November 2019).
JacobR, PEI




