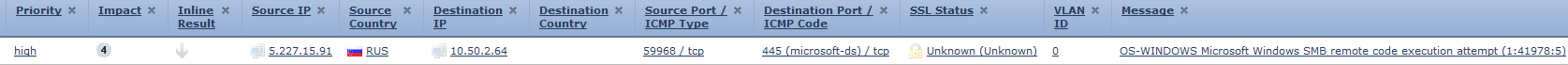
So I found an event today trying to get a remote code execution on one of the servers today. The attacker was from Russia address 5.227.15.91. I did a quick whois lookup on the IP address to see where the IP is really owned.
Here is what I found:
Results for 5.227.15.91 :
% This is the RIPE Database query service. % The objects are in RPSL format. % % The RIPE Database is subject to Terms and Conditions. % See http://www.ripe.net/db/support/db-terms-conditions.pdf % Note: this output has been filtered. % To receive output for a database update, use the "-B" flag. % Information related to '5.227.0.0 - 5.227.123.255' % Abuse contact for '5.227.0.0 - 5.227.123.255' is '[email protected]' inetnum: 5.227.0.0 - 5.227.123.255 netname: ISP-KOMSTAR-NN descr: CJS Company KOMSTAR-Regiony descr: Volga Region Branch in Nizhny Novgorod country: RU admin-c: SND-RIPE tech-c: SND-RIPE status: ASSIGNED PA mnt-by: AS8580-MNT mnt-by: MTU-NOC created: 2018-02-06T15:09:01Z last-modified: 2018-02-06T15:09:01Z source: RIPE role: SANDY ISP Network Operation Center address: Mobile TeleSystems OJSC Macro-region "Povolje" address: 168a, Gagarina prospect address: Nizhny Novgorod, 603009, Russia phone: +7 831 2728930 fax-no: +7 831 2728998 remarks: trouble: ------------------------------------------------- remarks: trouble: Please report SPAM and Network security issues to remarks: trouble: [email protected] remarks: trouble: ----------------------------------
So the attacker was from this IP block, or a comprised machine in this IP block. There are two ways to block this network from this and other future attacks. First, we can decide if we think this system/network has any business needs that require it to connect and reach Russia. If so we may just want to block the offending IP network range. Which from the whois, the network block is 5.227.0.0 – 5.227.123.255.
Creating a GEO Location Rule in Cisco Security Manager:
To block the traffic from the Cisco Security Management Server, we need to modify the access control policies. This is done through the Policies > Access Control. Then you need to find the policy that is running on the firewall in question. In my screenshots, the policy is called Basic.
Click the pencil Edit on the right hand side to modify the policy. Once in the policy, click the Plus to Add a Rule. ![]()
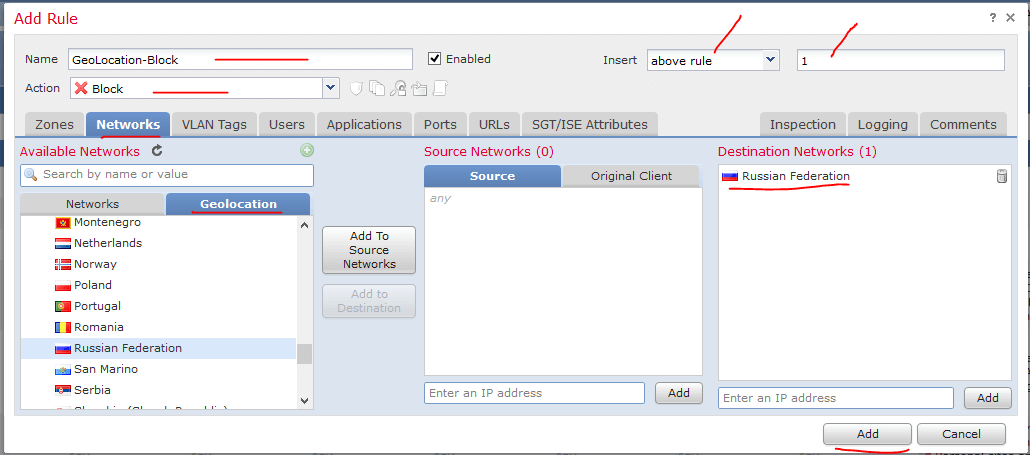
Give the rule a Name. In this case I used GeoLocation-Blocking.
Change the Action from Allow to Block.
Choose the Network tab, and the sub tab for GeoLocation. In the Geolocation area, find Europe and pick the country you want to block traffic to. In this case, we are using the Russian Federation. Add that to Destination Network. We could pick this as the source network, but if any system has malware and is trying to send traffic to the country, it would still be allowed. For this reason I picked the source as Any and block by the destination country.
Also, I suggest putting the rule at the top of the policy. So I have this rule as Insert Above the current rule 1.

We want to still log the connection attempts to Russia, so we will click over on the Logging tab on the right hand side. In the Logging section, click the radio box Log at Beginning of Connection.
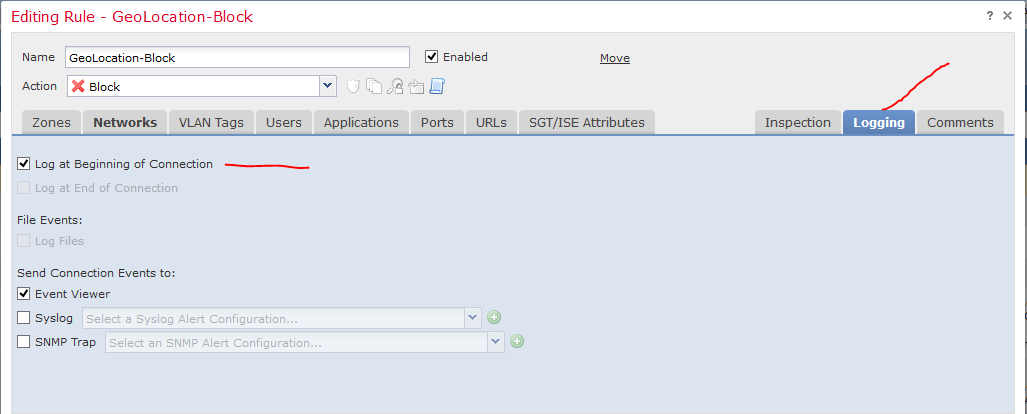
After all that, click the Add button. You now just need to click Save on the Access Control policy, and publish the new policy to the devices you want.
Looking for more tips on using the Cisco Security Management Center? Check out similar posts on how to create a policy to stop sensitive data from being sent out or how to set up anti-malware policies. Still can’t get enough? Subscribe to our blog below!
Jason Howe, PEI




